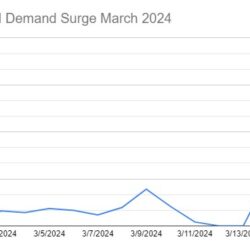
CSS allows HTML emails to change their content after they have been forwarded
[…] The email your manager received and forwarded to you was something completely innocent, such as a potential customer asking a few questions. All that email was supposed to achieve was being forwarded to you. However, the moment the email appeared in your inbox, it changed. The innocent pretext disappeared and the real phishing email Read more about CSS allows HTML emails to change their content after they have been forwarded[…]